Palo Alto 2FA with Duo
I've been working with Palo Alto firewalls pretty extensively for the last year. I decided it was time to get one for my homelab to keep increasing my skill set and to try out some new things. I migrated from a Ubiquiti USG to a PA-220 last week.
I have been using Apache Guacamole with Duo 2FA for primary remote access into my lab. With the implementation of the PAN, I decided to set up clientless VPN. I wanted to keep using Duo for 2FA. Duo already has this process outlined pretty well on their site, but I ran into a couple hurdles along the way that I wanted to outline for anyone else looking into this.
For the purpose of this post, I am going to assume that you Duo account is already created and you have at least one user enrolled to test with. Also, go ahead and set up the "Palo Alto SSL VPN" application in the Duo portal.
To get started, review Duo's documentation at https://duo.com/docs/paloalto.
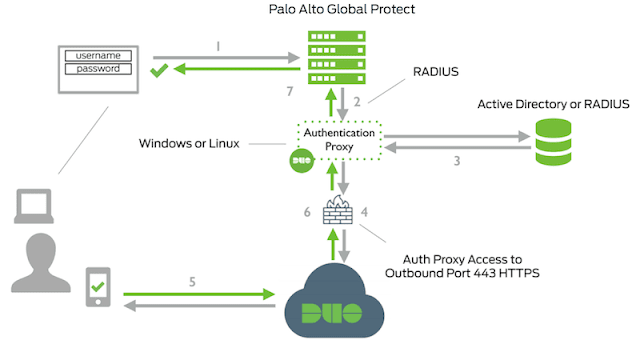
My deployment will use the Duo authentication proxy as a RADIUS proxy, which authenticates against my domain controllers via LDAP. So when I enter my AD credentials into the GP portal, the PA-220 sends my credentials to the Duo auth proxy via RADIUS, The proxy checks my credentials against LDAP, and if authenticated, sends a push notification to the Duo app on my phone. After I accept the authentication request, the proxy completes the RADIUS request and I am logged into the GP portal.
I deployed the Duo Authentication Proxy on a CentOS 7 minimal virtual machine running on an ESXi host. After the VM was installed and running, the process went as follows:
Update CentOS
# yum update
Install net-tools and wget
# yum install net-tools wget
Ensure that Python 2.6 or 2.7 is installed
# python --version
Install Duo Auth Proxy prerequisites:
# yum install gcc make openssl-devel python-devel libffi-devel
Download the latest version of the auth proxy
# wget https://dl.duosecurity.com/duoauthproxy-latest-src.tgz
Extract the files and build it
# tar xzf duoauthproxy-latest-src.tgz # cd duoauthproxy-version-src # make
Install the auth proxy (as root)
# cd duoauthproxy-build # ./install
Configure the config file.
# vi /opt/duoauthproxy/conf/authproxy.cfg
Here's mine as an example:
[main]
debug=true
[ad_client]
host=172.16.1.30 (IP address of primary domain controller)
host_2=172.16.1.31 (IP address of secondary domain controller)
service_account_username=sa_duo
service_account_password=supersecretpassword
search_dn=DC=homelab,DC=local
[radius_server_auto]
ikey=get this from the Palo Alto SSL VPN application in DUO
skey=get this from the Palo Alto SSL VPN application in DUO
api_host=get this from the Palo Alto SSL VPN application in DUO
radius_ip_1=172.16.1.10 (IP address of Palo Alto Management interface)
radius_secret_1=supersecretradiuskey
client=ad_client
port=1812
failmode=safe
client_ip_attr=paloalto
Start the proxy
# /opt/duoauthproxy/bin/authproxyctl start
Restart the proxy if changes are made to the config
# /opt/duoauthproxy/bin/authproxyctl restart
Configure firewalld to allow radius
# firewall-cmd --zone=public --add-service=radius --permanent
Restart firewalld
#firewall-cmd --reload
Now go ahead and create the service account for sa_duo (or whatever you name it) and apply the same password from authproxy.cfg.
Next, configure the Palo Alto firewall as follows:
Create a RADIUS server profile with the IP address of the Duo auth proxy and give it the same secret as configured in authproxy.cfg.
Set the timeout to 30, retries to 3, and protocol to PAP
Create a RADIUS authentication profile that points to the RADIUS server profile
Reference this Duo authentication profile in the GlobalProtect Portal and Gateway
Optionally, reference the Duo authentication profile in the administrator settings to apply Duo 2FA to the secure web UI.
To test, try logging into the GP portal or use the following command from CLI:
> test authentication authentication-profile DUO_AUTH_PROFILE username test password
Here are a couple interesting notes about the Duo Authentication Proxy. It does not use an interactive response page. Instead, by default it sends a push notification to the Duo Mobile app. Alternatively, you can override the push notification by requesting sms codes or a phone call from Duo.
username: test
password: password,sms
username: test
password: password,phone
I have been using Apache Guacamole with Duo 2FA for primary remote access into my lab. With the implementation of the PAN, I decided to set up clientless VPN. I wanted to keep using Duo for 2FA. Duo already has this process outlined pretty well on their site, but I ran into a couple hurdles along the way that I wanted to outline for anyone else looking into this.
For the purpose of this post, I am going to assume that you Duo account is already created and you have at least one user enrolled to test with. Also, go ahead and set up the "Palo Alto SSL VPN" application in the Duo portal.
To get started, review Duo's documentation at https://duo.com/docs/paloalto.
My deployment will use the Duo authentication proxy as a RADIUS proxy, which authenticates against my domain controllers via LDAP. So when I enter my AD credentials into the GP portal, the PA-220 sends my credentials to the Duo auth proxy via RADIUS, The proxy checks my credentials against LDAP, and if authenticated, sends a push notification to the Duo app on my phone. After I accept the authentication request, the proxy completes the RADIUS request and I am logged into the GP portal.
I deployed the Duo Authentication Proxy on a CentOS 7 minimal virtual machine running on an ESXi host. After the VM was installed and running, the process went as follows:
Update CentOS
# yum update
Install net-tools and wget
# yum install net-tools wget
Ensure that Python 2.6 or 2.7 is installed
# python --version
Install Duo Auth Proxy prerequisites:
# yum install gcc make openssl-devel python-devel libffi-devel
Download the latest version of the auth proxy
# wget https://dl.duosecurity.com/duoauthproxy-latest-src.tgz
Extract the files and build it
# tar xzf duoauthproxy-latest-src.tgz # cd duoauthproxy-version-src # make
Install the auth proxy (as root)
# cd duoauthproxy-build # ./install
Configure the config file.
# vi /opt/duoauthproxy/conf/authproxy.cfg
Here's mine as an example:
[main]
debug=true
[ad_client]
host=172.16.1.30 (IP address of primary domain controller)
host_2=172.16.1.31 (IP address of secondary domain controller)
service_account_username=sa_duo
service_account_password=supersecretpassword
search_dn=DC=homelab,DC=local
[radius_server_auto]
ikey=get this from the Palo Alto SSL VPN application in DUO
skey=get this from the Palo Alto SSL VPN application in DUO
api_host=get this from the Palo Alto SSL VPN application in DUO
radius_ip_1=172.16.1.10 (IP address of Palo Alto Management interface)
radius_secret_1=supersecretradiuskey
client=ad_client
port=1812
failmode=safe
client_ip_attr=paloalto
Start the proxy
# /opt/duoauthproxy/bin/authproxyctl start
Restart the proxy if changes are made to the config
# /opt/duoauthproxy/bin/authproxyctl restart
Configure firewalld to allow radius
# firewall-cmd --zone=public --add-service=radius --permanent
Restart firewalld
#firewall-cmd --reload
Now go ahead and create the service account for sa_duo (or whatever you name it) and apply the same password from authproxy.cfg.
Next, configure the Palo Alto firewall as follows:
Create a RADIUS server profile with the IP address of the Duo auth proxy and give it the same secret as configured in authproxy.cfg.
Set the timeout to 30, retries to 3, and protocol to PAP
Create a RADIUS authentication profile that points to the RADIUS server profile
Reference this Duo authentication profile in the GlobalProtect Portal and Gateway
Optionally, reference the Duo authentication profile in the administrator settings to apply Duo 2FA to the secure web UI.
To test, try logging into the GP portal or use the following command from CLI:
> test authentication authentication-profile DUO_AUTH_PROFILE username test password
Here are a couple interesting notes about the Duo Authentication Proxy. It does not use an interactive response page. Instead, by default it sends a push notification to the Duo Mobile app. Alternatively, you can override the push notification by requesting sms codes or a phone call from Duo.
username: test
password: password,sms
username: test
password: password,phone




Comments
Post a Comment